

OWASP stands for the Open Web Application Security Project. It is a nonprofit organization dedicated to improving the security of web applications and software. The primary focus of OWASP is on web application security, including vulnerabilities, threats, and best practices for secure development.
OWASP Top 10 is a widely recognized list of the top ten most critical web application security risks. This list is regularly updated to reflect emerging threats and vulnerabilities.
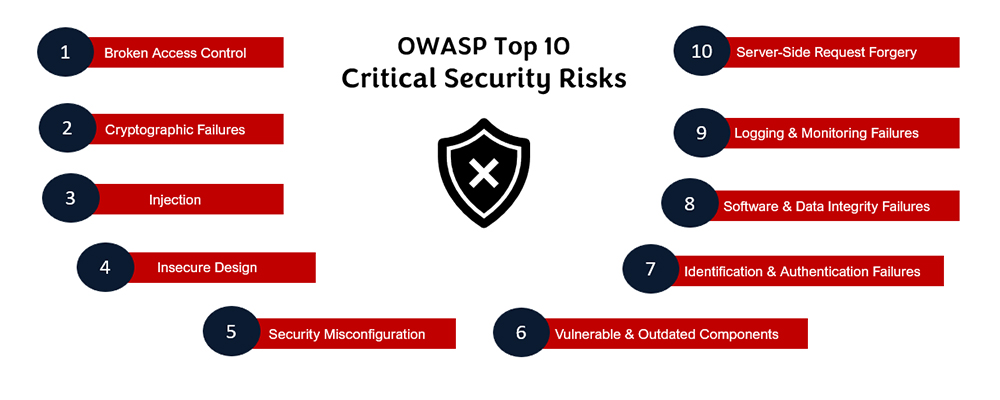
Broken Access Control is a security vulnerability that occurs when an application allows unauthorized users to access restricted resources or perform actions they should not be able to. When access control is broken, it can lead to various security risks, such as unauthorized data access, privilege escalation, vertical and horizontal access control issues, insecure direct object references (IDOR), and data leakage.
Cryptographic Failures refer to the vulnerabilities or weaknesses in cryptographic systems or algorithms that can be exploited by attackers to compromise the security and confidentiality of encrypted data. Cryptographic failures can occur due to various reasons, such as weak algorithms, insufficient key management, side-channel attacks, cryptanalysis, brute force attacks, and misconfiguration.
Injection attacks exploit weaknesses in an application's input validation and handling mechanisms. The attacker maliciously inserts untrusted data into a program, via input fields or parameters, with the intention of gaining unauthorized access to system data. Common types of injection attacks are SQL injection, cross-site scripting (XSS), LDAP injection, and XML injection.
Insecure Design refers to weaknesses in the design of a system or application that can be exploited by attackers to compromise security. Common examples of insecure design include are lack of authentication & authorization, inadequate input validation, weak cryptography, insecure communication, lack of error handling & logging, inadequate access controls, and vulnerable configuration defaults.
Security Misconfiguration refers to the improper configuration of security controls, settings, or protocols in an application, or network infrastructure, which can result in vulnerabilities and expose the system to potential security risks. For example, improper configuration of security headers in web applications can leave them vulnerable to various attacks, such as cross-site scripting (XSS), clickjacking, or content injection.
Vulnerable and Outdated Components can leave systems vulnerable to known vulnerabilities. Attackers can exploit these unpatched vulnerabilities to gain unauthorized access or execute malicious code.
Identification and Authentication Failure: Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, key, or session tokens.
Software and Data Integrity Failures: Code that does not protect against integrity failures like using plugins from untrusted sources that can lead to a compromise.
Insufficient Security Logging & Monitoring result in limited visibility into the activities and events occurring within the system. This makes it challenging to detect and investigate security incidents and identify malicious activities. Moreover, many industries and jurisdictions have regulatory requirements that mandate logging and monitoring practices to protect sensitive data and ensure compliance. Failure to implement adequate logging and monitoring measures can lead to legal and regulatory consequences, including financial penalties and reputational damage.
Server-Side Request Forgery (SSRF): occurs when an application fetches resources without validating the destination URL.