A hacker is an individual who possesses advanced knowledge and skills in computer systems, networks, and software.
They are proficient in identifying vulnerabilities, exploiting weaknesses, and bypassing security measures to gain unauthorized access to computer systems, networks, or digital devices.
The term "hacker" is often used to describe individuals with varying levels of expertise and intentions. Below is different levels or categories of hackers:
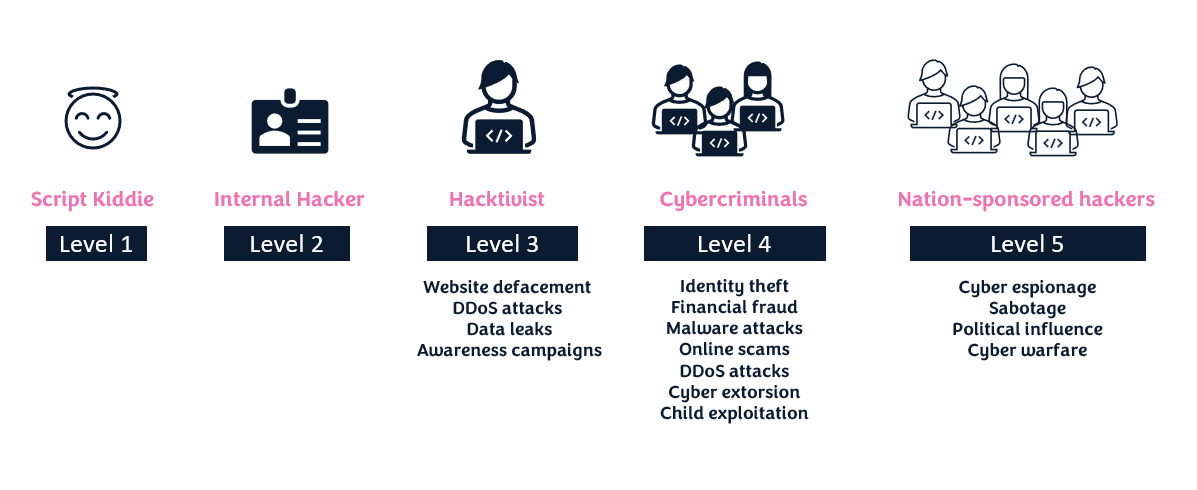
Script kiddie: are individuals with limited technical skills and knowledge who rely on pre-existing hacking tools and scripts to carry out attacks or malicious activities.
They may exploit known vulnerabilities or use pre-built scripts to launch attacks against systems or networks.
Their actions are often driven by curiosity, a desire for recognition, or a misguided sense of adventure.
Internal hacker:
refers to an individual who carries out hacking activities from within an organization to which they have authorized access.
Unlike external hackers who attempt to breach a system from outside, insider hackers already have legitimate access to the organization's network, systems, or data due to their position in the organization.
Insider hackers can pose a significant threat to organizations as they have intimate knowledge of the systems, networks, and security measures in place.
They may exploit their authorized access to carry out unauthorized activities, steal sensitive information, sabotage systems, or manipulate data for personal gain or malicious intent.
Insider hackers may include disgruntled employees, contractors, or individuals with privileged access.
Hacktivist:
refers to an individual or group that typically uses their technical skills and knowledge to carry out online actions or campaigns in support of their beliefs or to raise awareness about specific issues.
-
Website Defacement:
Hacktivists may deface websites by modifying their content or displaying messages related to their cause. This can be done to draw attention, make a statement, or protest against a particular organization, government, or policy.
-
(DDoS) Attacks:
Hacktivists may use DDoS attacks to overload websites or online services with a flood of traffic, rendering them inaccessible to regular users.
This type of attack aims to disrupt the operations of a targeted entity as a form of protest or to bring attention to an issue.
-
Data Leaks and Information Disclosure:
Hacktivists may hack into systems or databases to obtain sensitive information and then release it publicly.
This can include exposing confidential documents, emails, or personal information to shed light on perceived wrongdoing or to reveal information that they believe should be made public.
-
Awareness Campaigns:
Hacktivists may use online platforms, social media, and other digital channels to spread awareness, advocate for causes, or rally support.
Cybercriminal:
refers to an individual or group of individuals who engage in criminal activities using digital technologies and the internet.
Cybercriminals exploit vulnerabilities in computer systems, networks, and online platforms to commit various types of crimes, often with the intent of financial gain.
Common types of cybercrimes perpetrated by cybercriminals include:
-
Identity Theft:
Cybercriminals steal personal information, such as social security numbers, credit card details, or login credentials, with the aim of assuming someone's identity for fraudulent purposes.
-
Financial Fraud:
Cybercriminals use various techniques like phishing, spoofing, or malware to deceive individuals or organizations into providing sensitive financial information or to carry out unauthorized financial transactions.
-
Malware Attacks:
Cybercriminals develop and distribute malicious software, such as viruses, worms, Trojans, or ransomware, to gain unauthorized access, compromise systems, steal data, or extort money from victims.
-
Online Scams:
Cybercriminals create fraudulent websites, emails, or advertisements to deceive individuals into providing money or personal information under false pretenses.
This can include lottery scams, romance scams, or fake job offers.
-
Distributed Denial of Service (DDoS) Attacks:
Cybercriminals orchestrate DDoS attacks to overwhelm targeted websites or online services, causing disruption and financial losses.
-
Cyber Extortion:
Cybercriminals may use stolen data, ransomware, or threats to disrupt or harm organizations or individuals, demanding payment in exchange for stopping or mitigating the damage.
-
Child Exploitation:
Cybercriminals engage in the production, distribution, or consumption of child pornography, or they may groom and exploit children for sexual purposes through online platforms.
Nation-sponsored hackers:
are individuals or groups who carry out hacking activities on behalf of a government or nation-state.
These hackers are supported, funded, or directed by a government entity to conduct cyber operations that serve their national interests, political objectives, or strategic goals.
-
Cyber Espionage: Nation-sponsored hackers engage in intelligence-gathering activities by infiltrating computer systems, networks, or organizations to gain access to sensitive information.
This can include government secrets, classified documents, intellectual property, or military intelligence.
-
Sabotage and Disruption: Nation-sponsored hackers may target critical infrastructure, such as power grids, transportation systems, or financial networks, to disrupt operations or cause damage.
These attacks can have significant consequences for national security or economic stability.
-
Political Influence: Nation-sponsored hackers may engage in activities to influence political processes, elections, or public opinion in other countries.
This can involve hacking into political party networks, leaking sensitive information, or spreading disinformation.
-
Cyber Warfare: Nation-sponsored hackers may be involved in offensive cyber operations during times of conflict.
This can include disrupting enemy communication networks, conducting cyberattacks against military targets, or engaging in information warfare.


